Register a custom web app
Sign in to the Azure portal
Sign in to the Azure portal as an admin.
Select a tenant
If you have access to multiple tenants, use the Directory + subscription filter in the top menu to select the tenant in which you want to register an application.
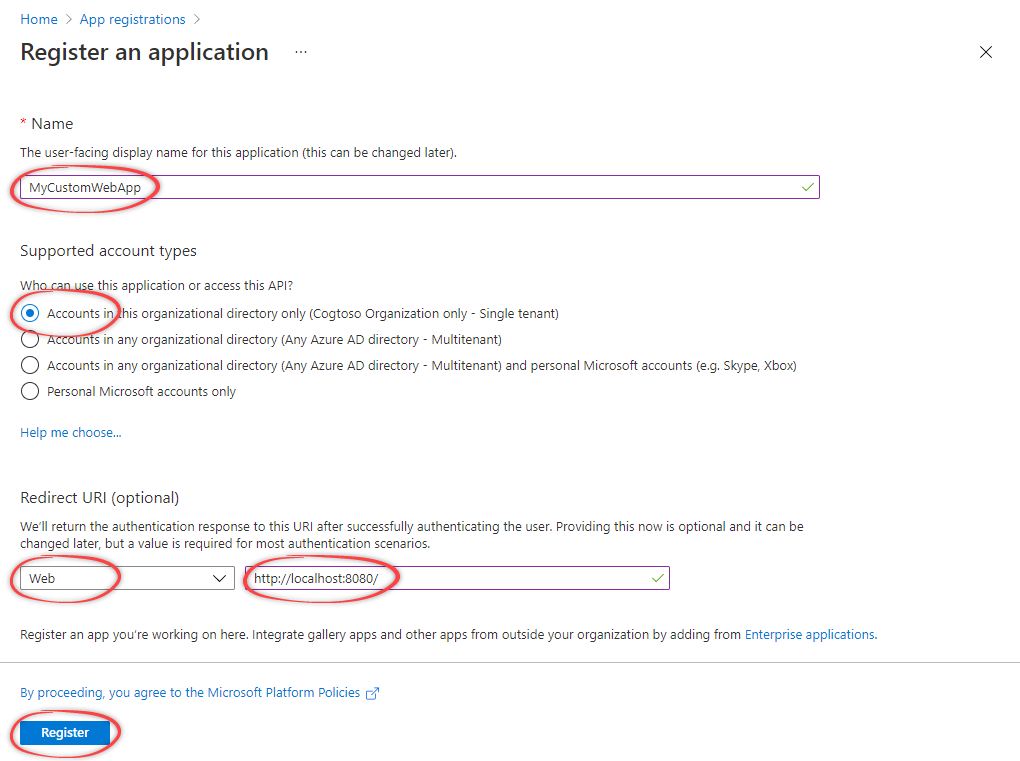
Select name and type
Specify the name and select an account type. Select the first option unless your organization’s preferences specify otherwise.
Select redirect URI
Under Redirect URI (optional), select Web and specify the redirect URI. Typically, this is the URL of your web app, or localhost for development. You can add more redirect URIs under Manage > Authentication.
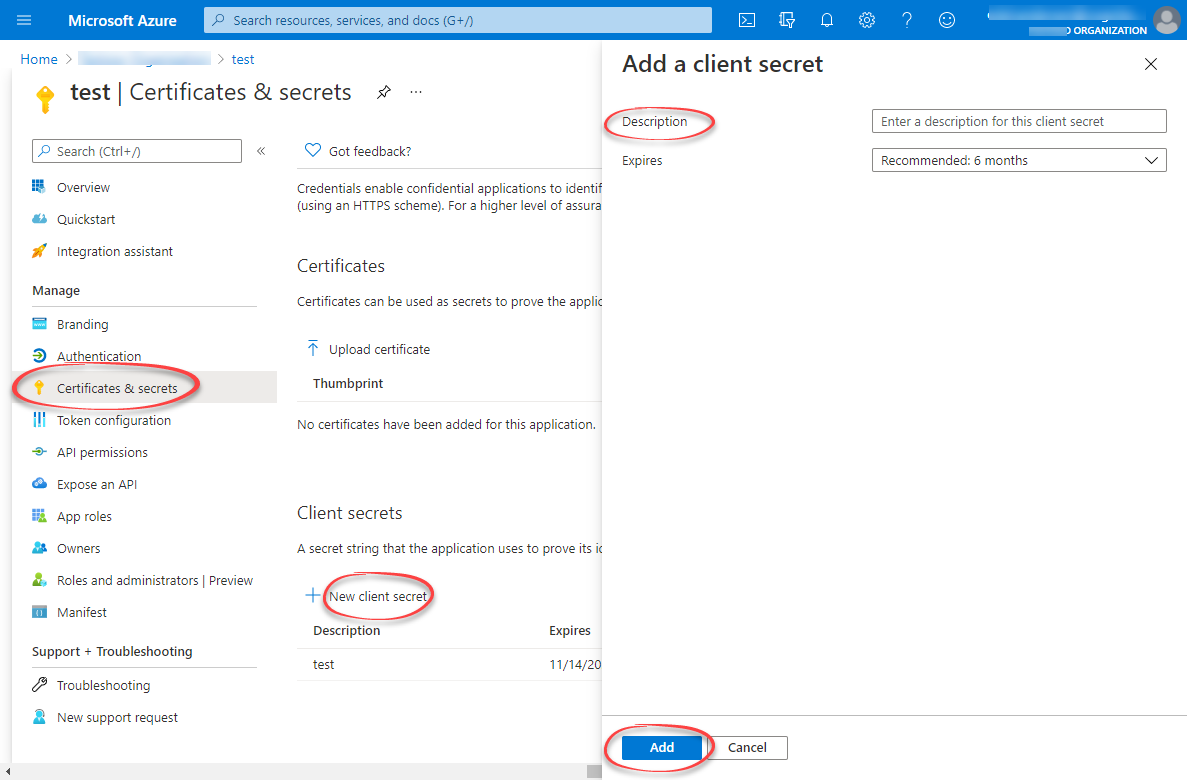
Create a client secret
Configure the client secret
Enter a description and how long the client secret will be valid. Then, select Add.
Configure API permissions
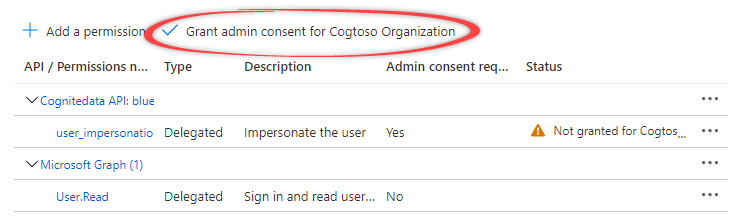
Navigate to API permissions
Under Manage, select API permissions. The Microsoft Graph
User.Read permissions should already be selected.Select the Cognite API
Select + Add a permission. In the side panel, open the APIs my organization uses tab, and select the Cognite API, for example
westeurope-1.Select application permissions
For Delegated permissions, select the required permissions for your application, for example
user_impersonation. The delegated permissions filter the permissions a user has based on group memberships, but don’t add any permissions.To use the token inspection endpoint, select IDENTITY.Learn more about the available permissions here.