Step 1: Create a group in Microsoft Entra ID
Sign in to the Azure portal
Sign it to your Azure portal > Search for and select Microsoft Entra ID.
Create a group
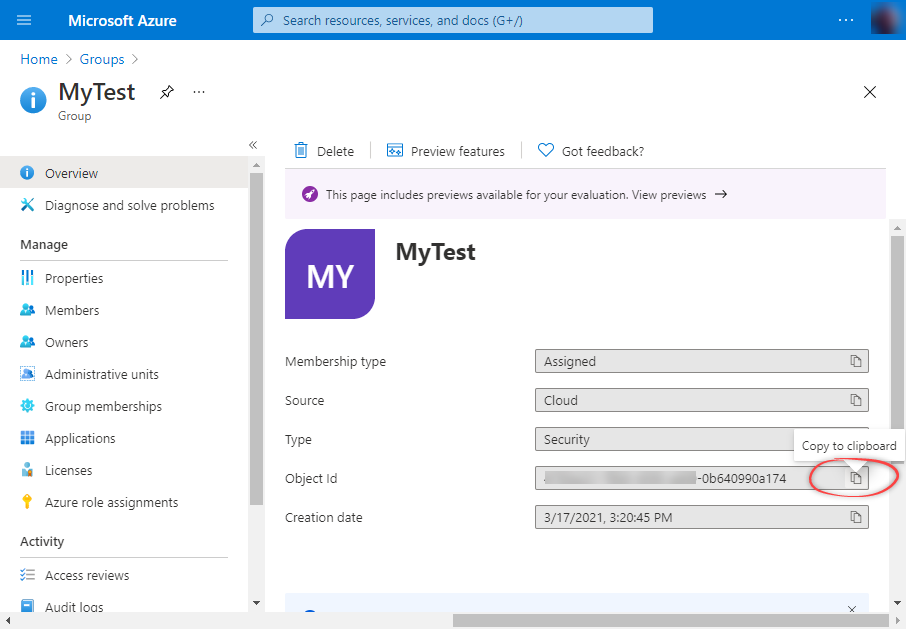
In the New Group window, select Security as the Group type, enter a Group name, and then select Create.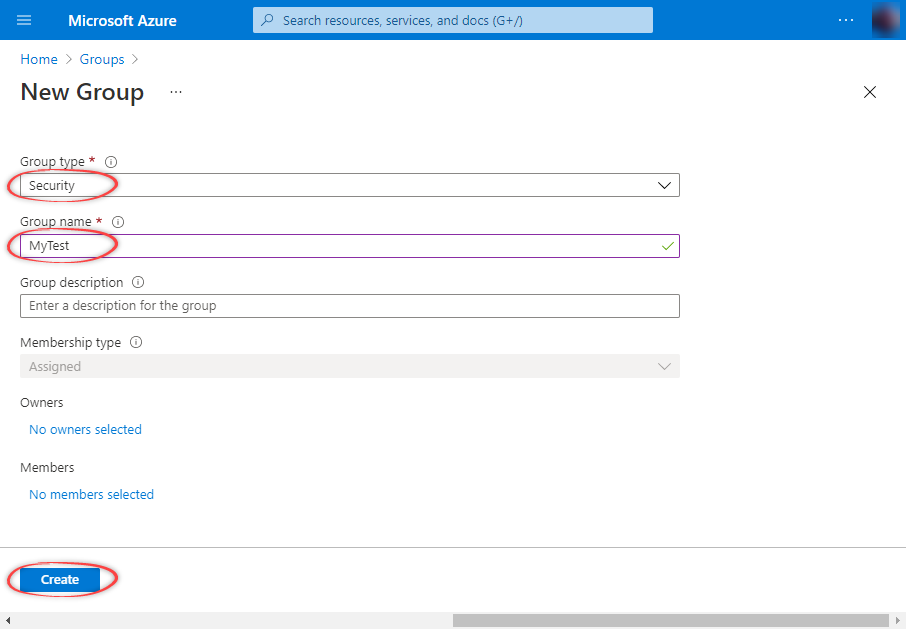

Add members
Select the group to open it, add members - users or service accounts, to the group (service accounts are called applications).
Step 2: Create a group in CDF and link it to the Microsoft Entra ID group
Sign in to Cognite Data Fusion
Sign in to Cognite Data Fusion as an admin.
Link the group
In Members select Externally managed, and in the Source ID field, enter the Object Id for the Microsoft Entra ID (ME_ID) group exactly as it exists in ME-ID. It will link the CDF group to an Azure AD group.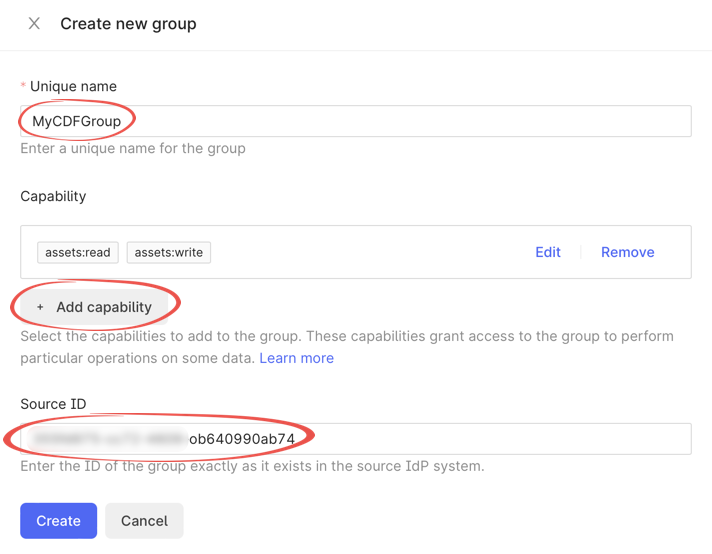

Link the group to an application
In the Application (Client) ID dropdown, select the existing or create a new Application (Client) ID to link groups to specific applications to improve query efficiency. Application (Client) ID is a unique public identifier for an application registered with an authorization server. You can set more than one Application (Client) ID for a group.When users make a query to CDF, their Effective Access (EA) is determined by the union of all capabilities and scopes from the groups they’re members of. When users make a query from an application, only the groups linked to that application are considered for EA.
This feature is currently supported only for CDF organizations configured with Microsoft Entra ID as their identity provider (IdP).