Before you start
To use the different grant types (Implicit, Authorization code (with PKCE)) with your requests in Postman, you need to grant access to a multi-tenant app in Entra ID to use CDF with Postman. To grant access, you must be an Entra ID tenant administrator. Follow the steps in How to register Cognite API to register the app. When you have registered the app, you can sign in with your Entra ID credentials. Before you set up authorization in Postman, configure your Entra ID application:Locate your tenant and application IDs
Go to Entra ID and find your Tenant ID and Application (client) ID in the overview page.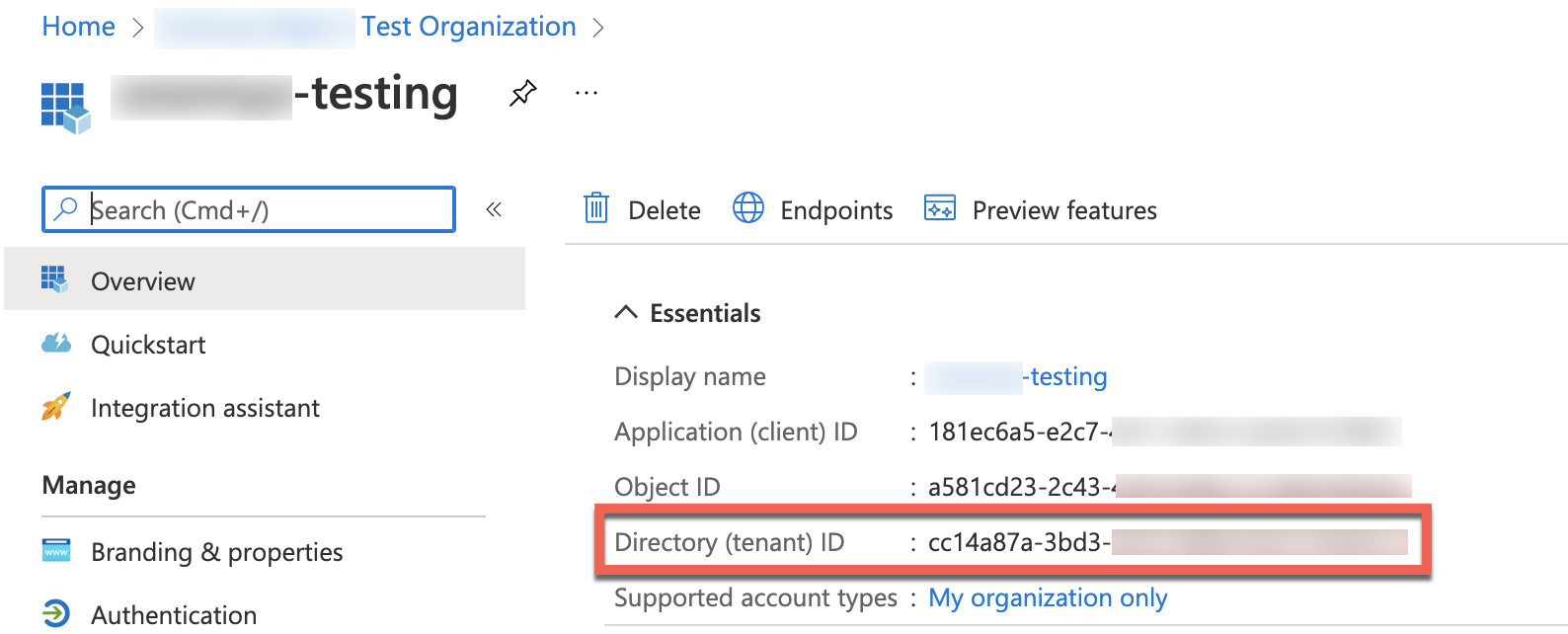

Create a client secret
In the App registrations section, create a New client secret under Certificates & secrets in the left menu.Select + New client secret, enter a description, choose an expiry period, and select Add.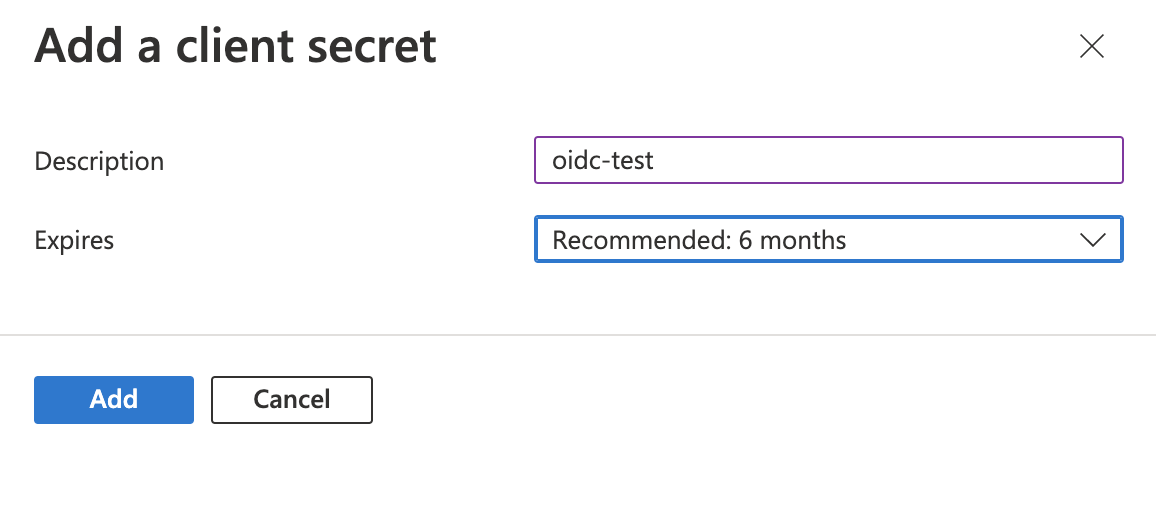

Set up Postman
Import your Postman collection
Download the Cognite OpenAPI specification.In Postman, select Import and drag the file to the import modal.In View Import Settings, configure the import: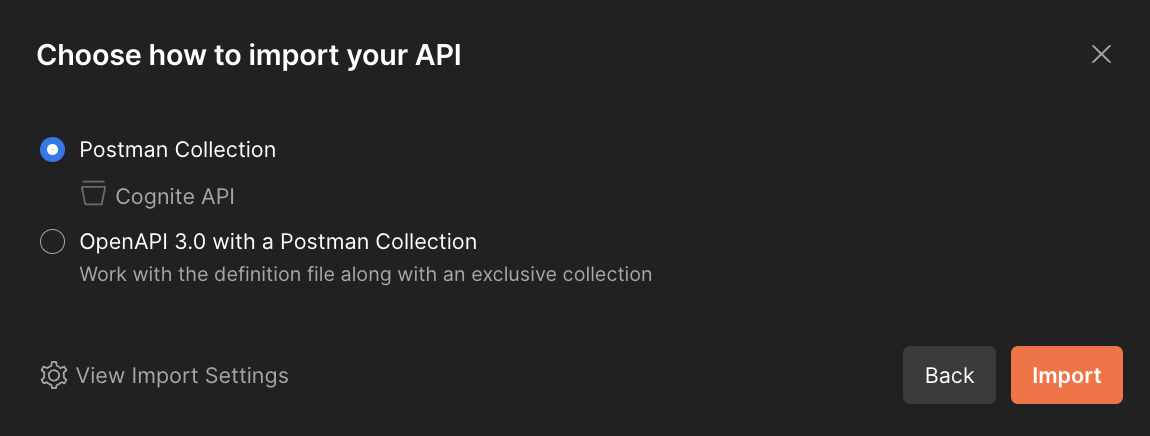 Select Continue > Import to complete the import.
Select Continue > Import to complete the import.
- Set Folder organization to Tags
- Turn off the Enable optional parameters option
- Turn on the Always inherit authentication option

The Cognite API collection is now available in your Postman workspace.
Set up environment variables
Navigate to Environments on the left sidebar and select + Create new Environment. Give your environment a descriptive name.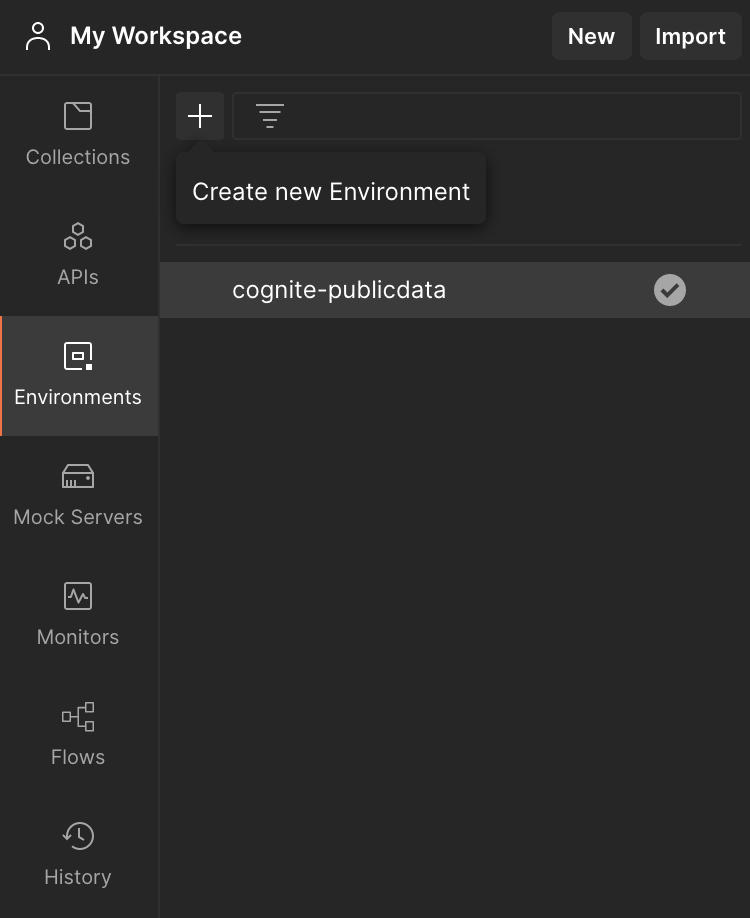 Add the following variables to your environment:
Add the following variables to your environment:

- tenant-id: Your Directory (tenant) ID from Entra ID.
- token: Leave this blank. OAuth 2.0 will populate it automatically when you authenticate.
-
baseUrl: Set to
https://{{cluster}}.cognitedata.com/api/v1/projects/{{project}}where cluster is your CDF instance location. If you don’t know the cluster name, contact Cognite support. For Open Industrial Data, useapi. - project: Your CDF project name.
We recommend working with the current value of variables to prevent sharing sensitive information with your team.
Your environment is configured and ready to use with the Cognite API collection.
Configure OAuth 2.0 authorization
With OAuth 2.0, you retrieve an API access token and use it to authenticate future API requests.Navigate to the Authorization tab in the collection overview and configure: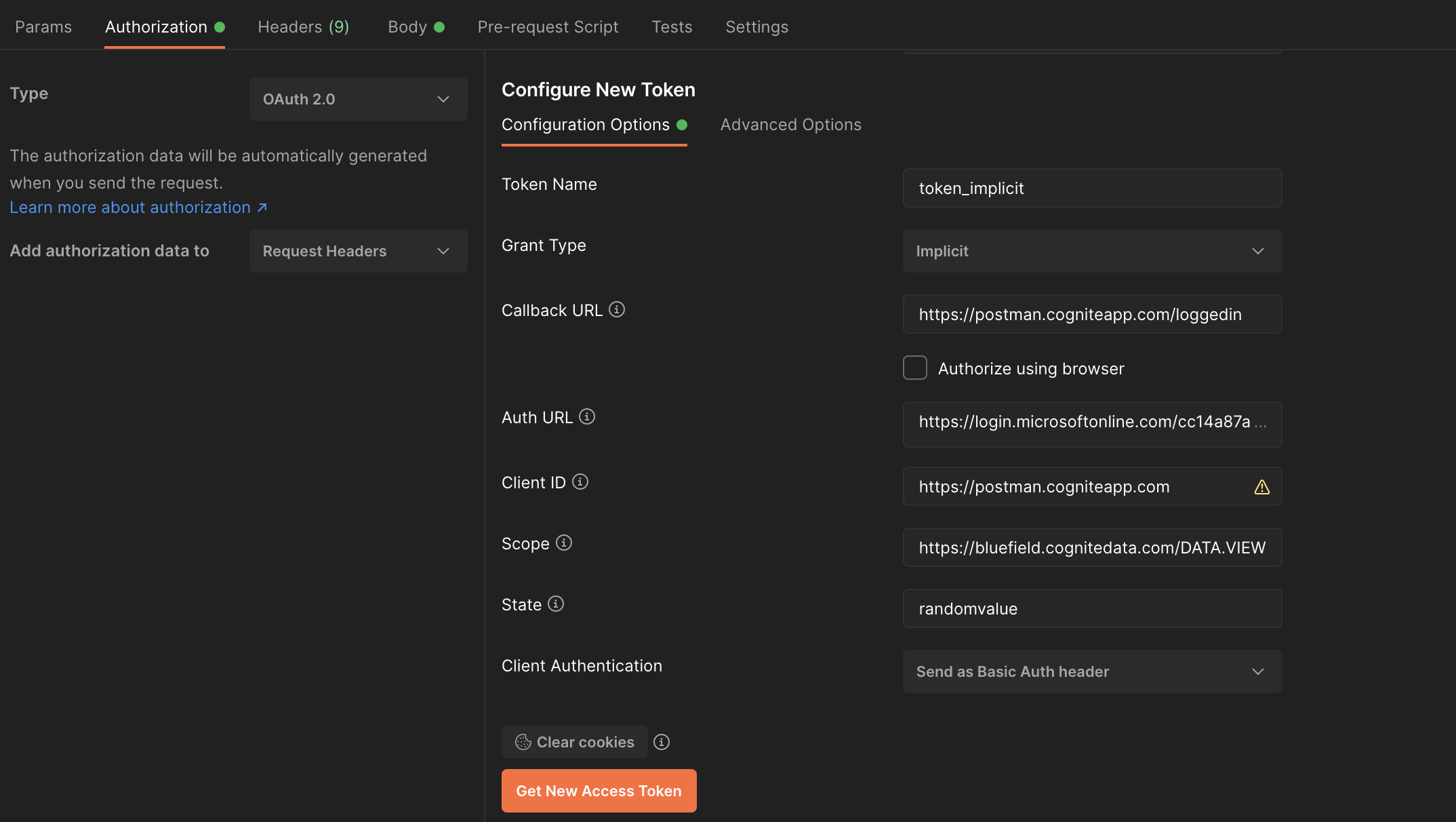 Select Get New Access Token > Proceed > Use Token.
Select Get New Access Token > Proceed > Use Token.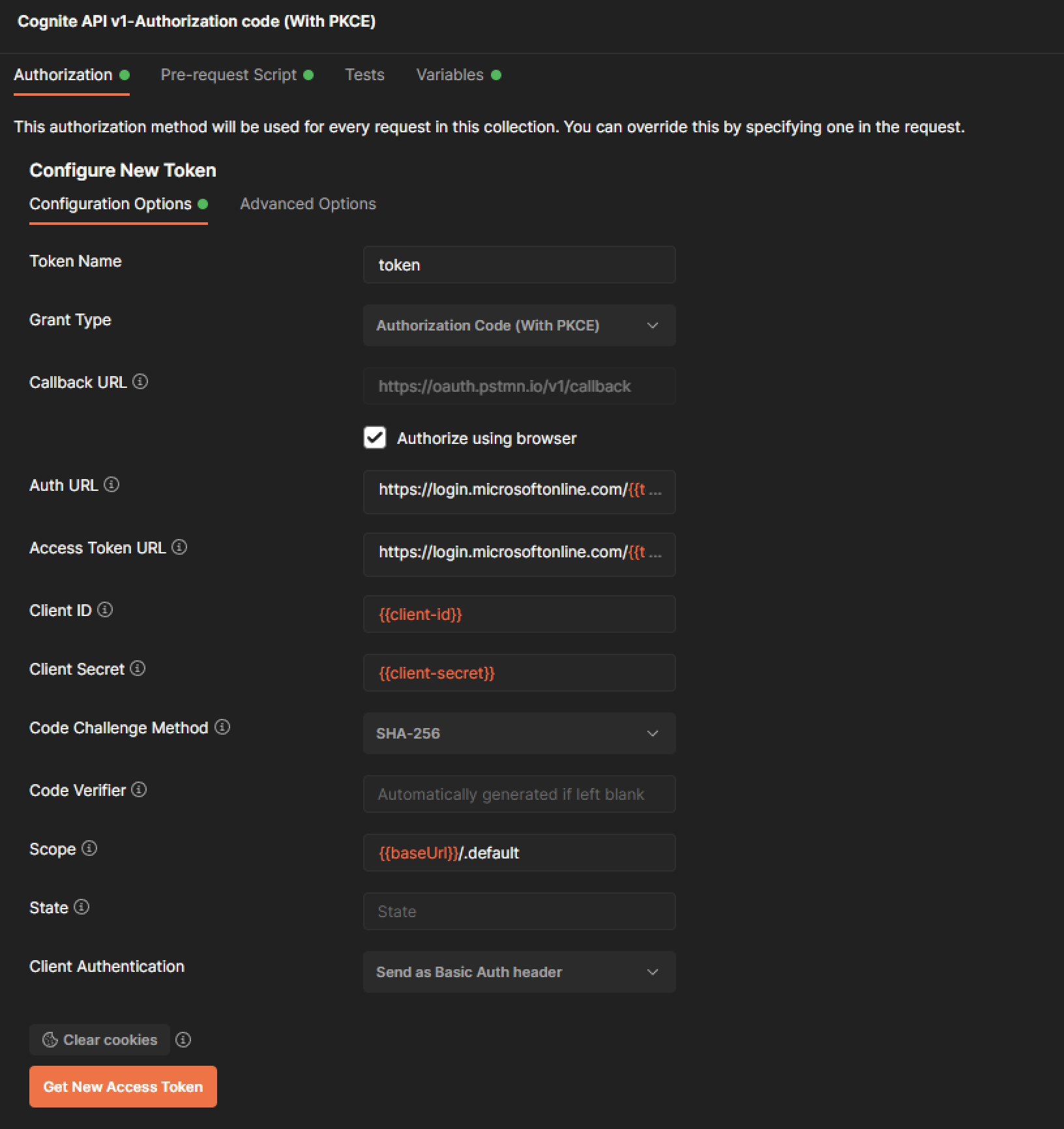 Select Get New Access Token > Proceed > Use Token.
Select Get New Access Token > Proceed > Use Token.
- Set Type to OAuth 2.0
- Set Add authorization data to to Request Headers
Choose the OAuth 2.0 grant type that matches your use case: Implicit or Authorization Code (With PKCE). For more details on authentication flows, see Configure applications and the authentication flows.
Implicit
Select Configure New Token and specify these configuration options:- Token Name: Enter a descriptive name for your token.
- Grant Type: Select Implicit.
- Callback URL: Enter
https://postman.cogniteapp.com/loggedin.
If you select the Authorise using browser checkbox, the Callback URL auto-populates. Once your application is authorized, you’ll be redirected to this URL.
- Auth URL: Enter
https://login.microsoftonline.com/{{tenant-id}}/oauth2/v2.0/authorize(replace{{tenant-id}}with your tenant ID). - Client ID: Enter
https://postman.cogniteapp.com. - Scope: Enter
https://{{cluster}}.cognitedata.com/followed by one of:default,user_impersonation,DATA.VIEW, orIDENTITY.
The
user_impersonation scope grants all permissions assigned to the user. The DATA.VIEW scope grants read-only access to CDF resources like files, time series, and RAW. Learn more about Access token scopes.- Client Authentication: Select Send as Basic Auth header.

You have configured a new token using the Implicit grant type.
Authorization Code (With PKCE)
Select Configure New Token and specify these configuration options:- Token Name: Enter a descriptive name for your token.
- Grant Type: Select Authorization Code (With PKCE).
- Callback URL: Enter
https://oauth.pstmn.io/v1/callback. - Auth URL: Enter
https://login.microsoftonline.com/{{tenant-id}}/oauth2/v2.0/authorize(replace{{tenant-id}}with your tenant ID). - Access Token URL: Enter
https://login.microsoftonline.com/{{tenant-id}}/oauth2/v2.0/token(replace{{tenant-id}}with your tenant ID). - Client ID: Enter your application’s client ID from Entra ID.
- Client Secret: Enter the client secret you created earlier.
- Code Challenge Method: Choose either
SHA-256orPlainalgorithm. - Code Verifier: Leave blank to auto-generate, or enter a 43-128 character string to connect the authorization request to the token request.
- Scope: Enter
https://{{cluster}}.cognitedata.com/followed by one of:default,user_impersonation,DATA.VIEW, orIDENTITY. - State: Enter a random value to prevent cross-site request forgery attacks.
- Client Authentication: Select Send as Basic Auth header.

You have configured a new token using Authorization Code (With PKCE) grant type. You’re now ready to use Postman with OIDC as the authentication method.