Setup and administration for Microsoft Entra ID
You can use OpenID Connect and your existing identity provider (IdP) framework to manage access to Cognite Data Fusion data securely. This article explains how to register and configure apps in Microsoft Entra ID (ME-ID) to use with data integration services such as extractors and connectors, or scheduled custom scripts.
To perform the steps below, you must be an administrator of Microsoft Entra ID.
Before you start
Make sure you have registered the Cognite API and the CDF in Microsoft Entra ID and set up Microsoft Entra ID and CDF groups to control access to CDF data.
Step 1: Register an app in Microsoft Entra ID
Cognite recommends that you register one app per integration service and per environment. For example, we recommend 3 app registrations to run one extractor or connector in dev, test, and prod environments.
- Sign in to the Azure portal as an admin.
- If you have access to multiple tenants, use the Directory + subscription filter (
 ) in the top menu to select the tenant in which you want to register an application.
) in the top menu to select the tenant in which you want to register an application. - Search for and select Microsoft Entra ID.
- Under Manage, select App registrations > New registrations.
- In the Register an application window, enter the app name and select Register.
- Copy and make a note of the Application (client) ID. You'll need this value for authentication when reading and writing data with your integration service.
- Under Manage, select Certificates & secrets > New client secret.
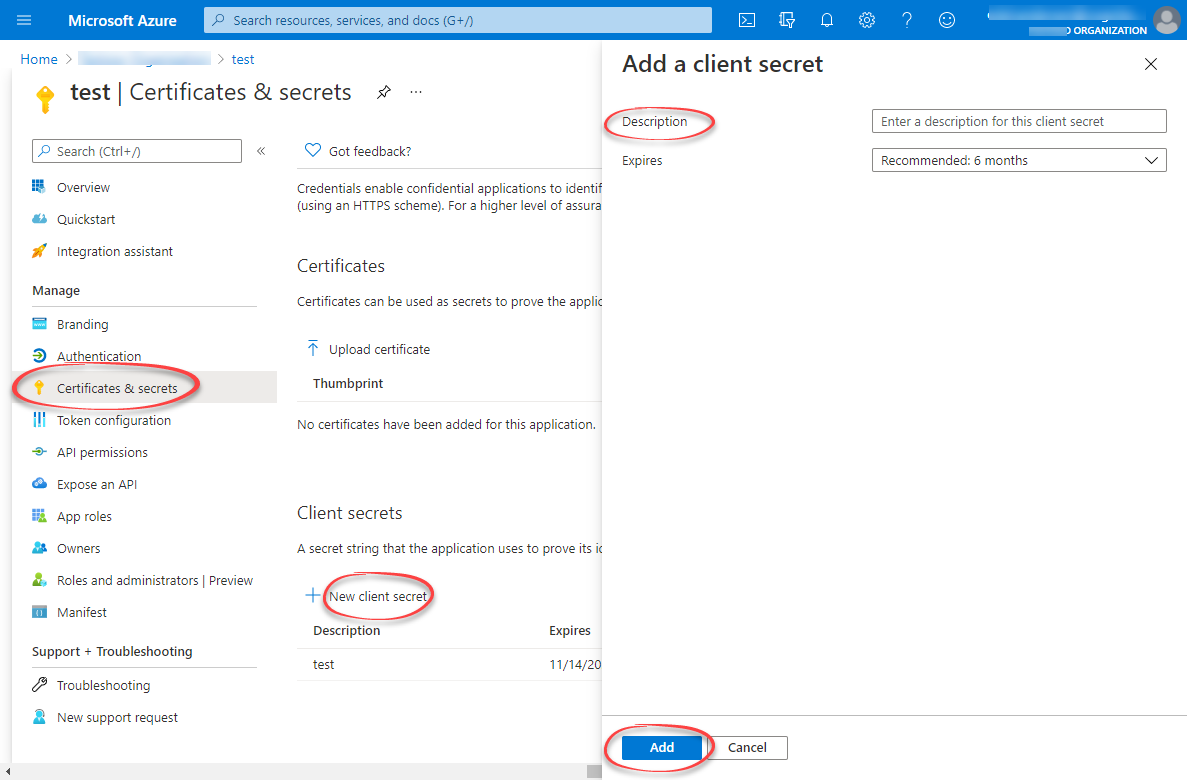
-
Enter a client secret description and an expiry time, and then select Add.
-
Copy and make a note of the client secret in the Value field.
ImportantMake sure you copy this value now. This value will be hidden after you leave this page.
Step 2: Create a group in Microsoft Entra ID and add the registered app as its member
- Open the overview window in Microsoft Entra ID and select Manage > Groups.
- Create a group. Read more here.
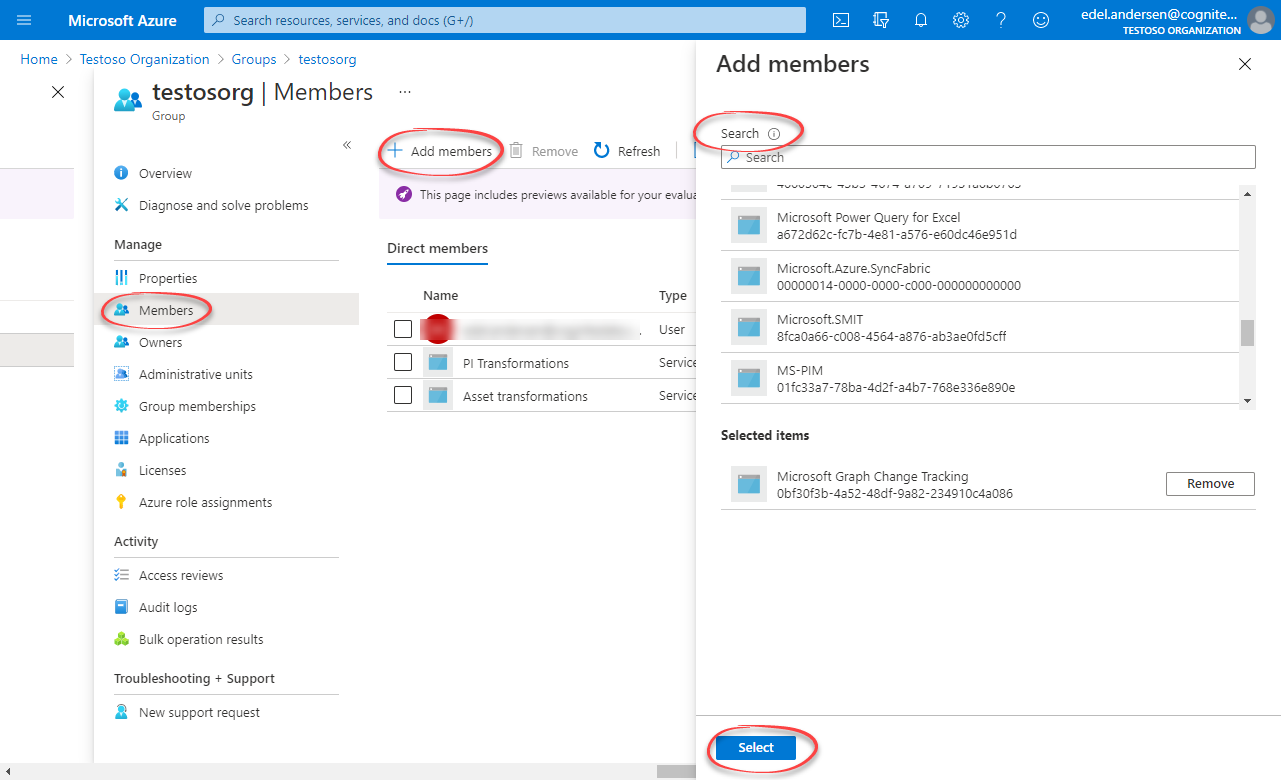
- Open the group. Under Manage, select Members > Add members.
- Find the app you created above and click Select.
- Add all users you want to have access to the integration service as members.
- Return to the overview, and then copy and make a note of the Object Id.
Step 3: Create a group in CDF and link to the Microsoft Entra ID group
- Sign in to CDF as an admin and navigate to Access > Groups > Create new group.
- In the Create a new group window, enter the group name (case sensitive).
- Add the necessary capabilities for your integration service:
- For extractors, see Extractor capabilities
- For connectors, see Connector capabilities
- Link the group to a Microsoft Entra ID group:
- In the Source ID field, enter the Object Id for the AAD group exactly as it exists in AAD. You can use the same group Id for multiple services.
- In the Source name field, enter the name of the group in Microsoft Entra ID.
Step 4: Deploy your integration service
Configure and deploy your integration service according to the documentation:
- For extractors, see the extractors documentation
- For connectors, see the connectors documentation