To perform the steps below, you must be an administrator of Microsoft Entra ID.
Before you start
Make sure you have registered the Cognite API and the CDF in Microsoft Entra ID and set up Microsoft Entra ID and CDF groups to control access to CDF data.Step 1: Register an app in Microsoft Entra ID
Sign in to the Azure portal
Sign in to the Azure portal as an admin.
Select a tenant
If you have access to multiple tenants, use the Directory + subscription filter in the top menu to select the tenant in which you want to register an application.
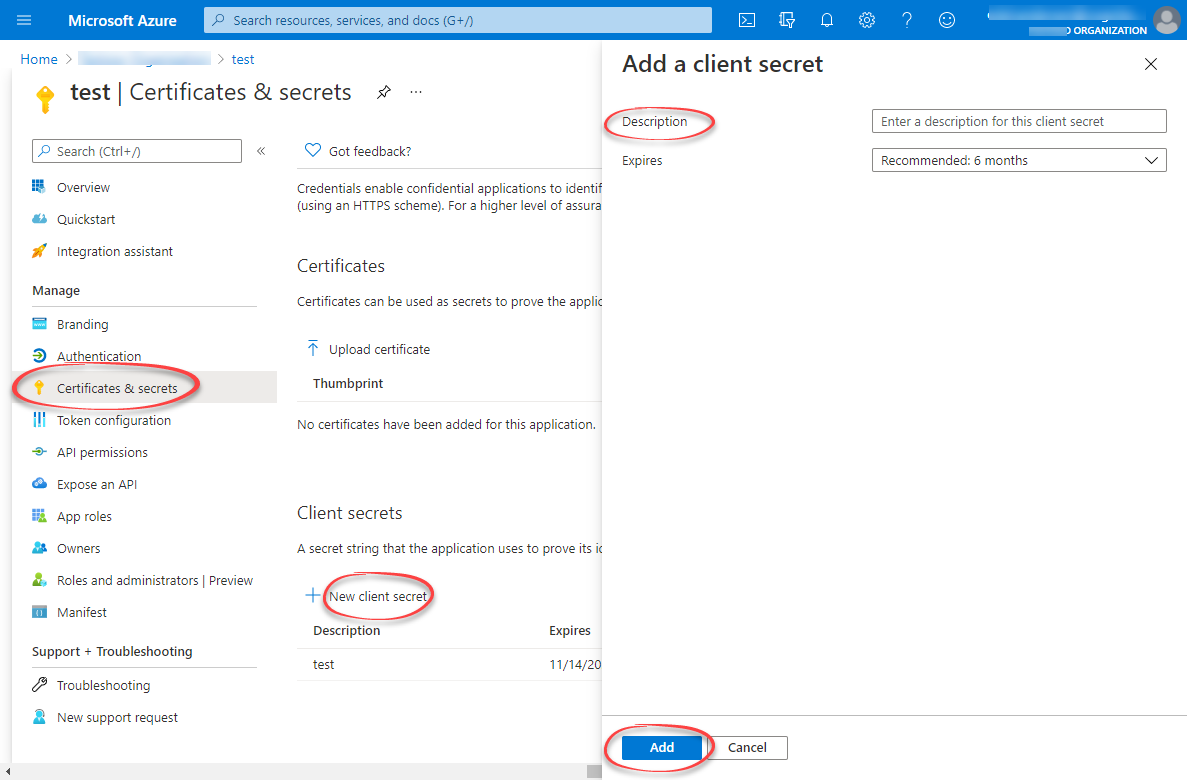
Register an application
In the Register an application window, enter the app name and select Register.
Copy the Application ID
Copy and make a note of the Application (client) ID. You’ll need this value for authentication when reading and writing data with your integration service.
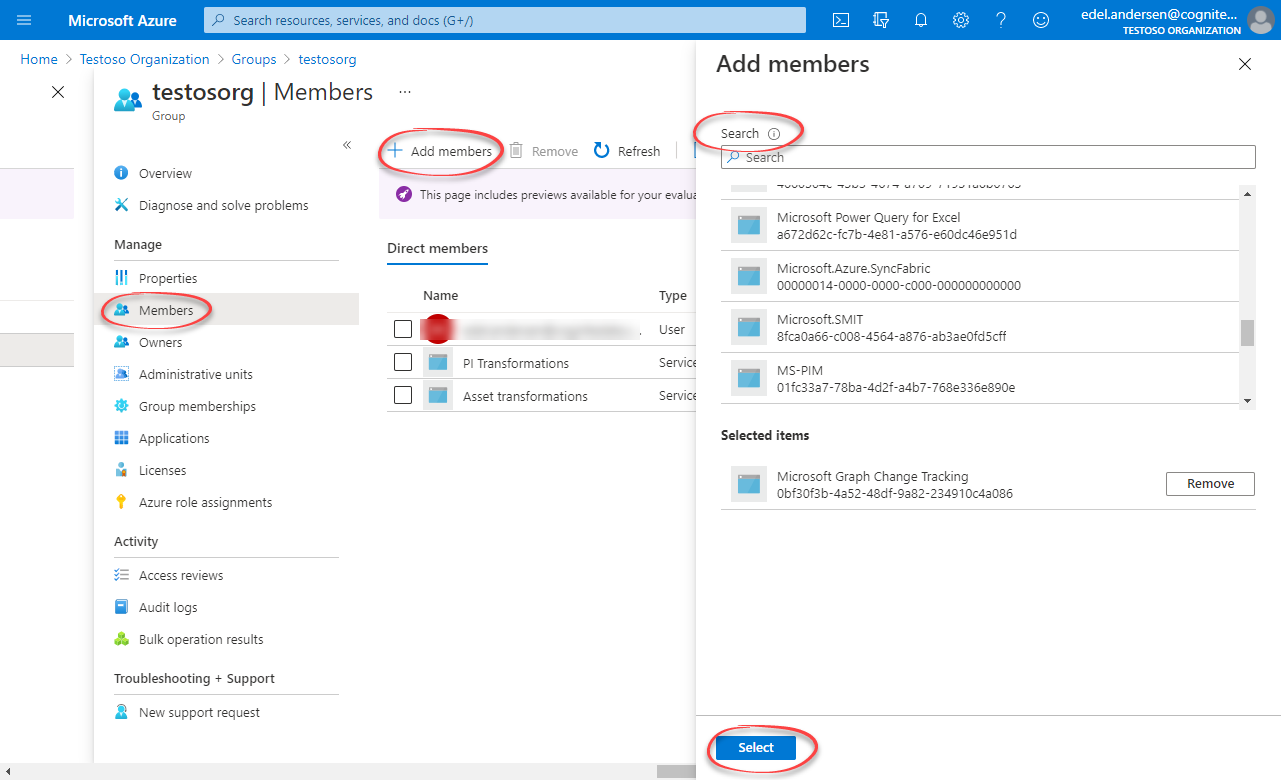
Step 2: Create a group in Microsoft Entra ID and add the registered app as its member
Create a group
Create a group. Read more here.
Step 3: Create a group in CDF and link to the Microsoft Entra ID group
Add capabilities
Add the necessary capabilities for your integration service:
- For extractors, see extractor capabilities.
- For connectors, see connector capabilities.
Step 4: Deploy your integration service
Configure and deploy your integration service according to the documentation:- For extractors, see the extractors documentation.
- For connectors, see the connectors documentation.